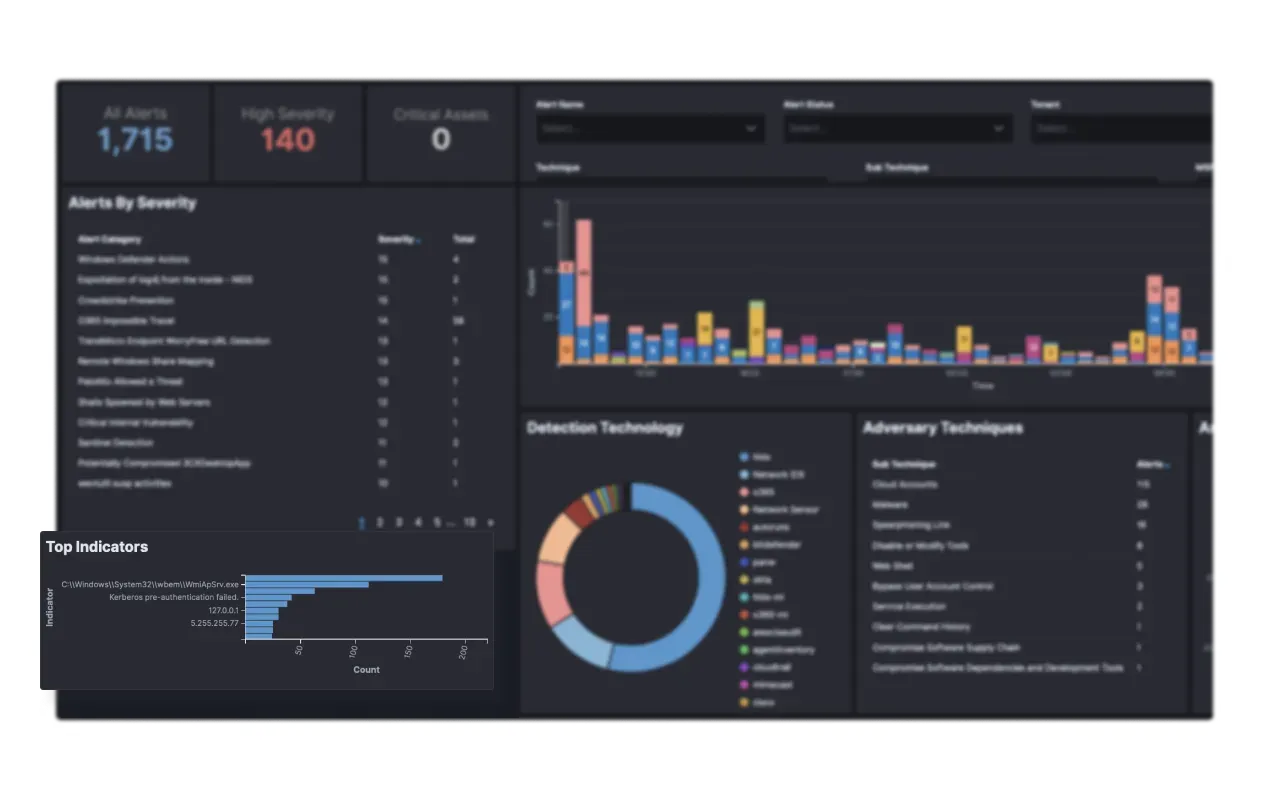
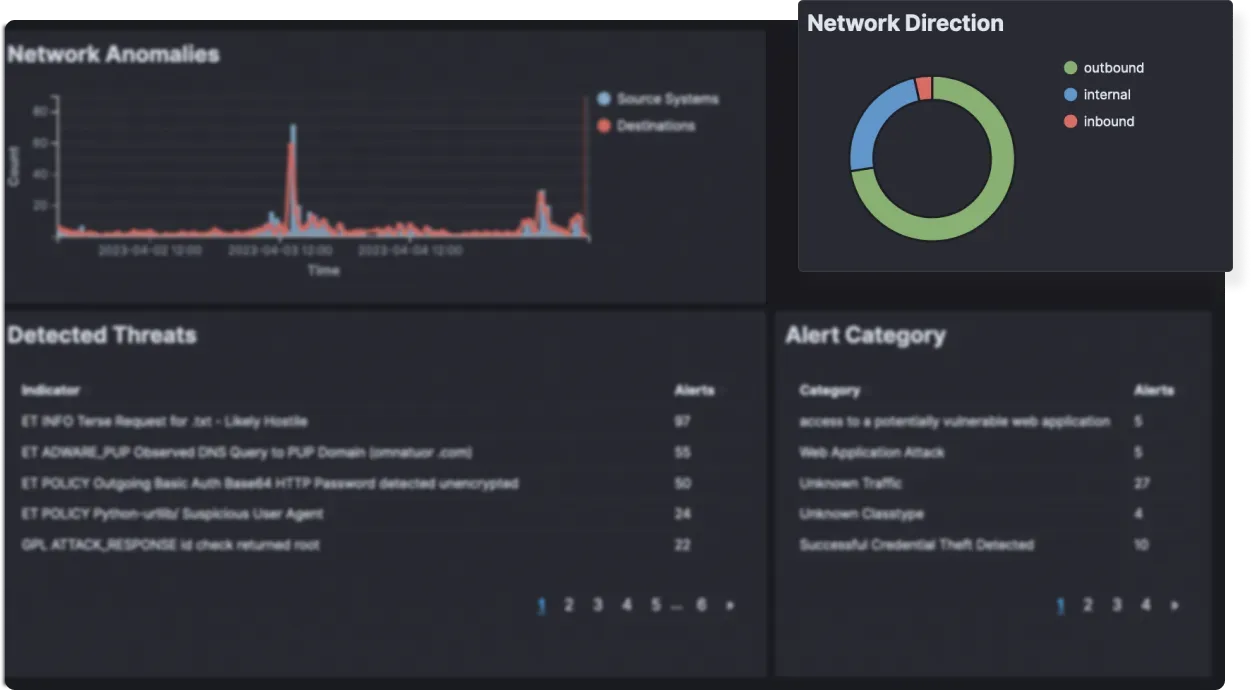
Everyone is being hacked despite spending millions on cyber security.
It seems like every vendor has a solution on how to protect your business. The promise is a simple and reliable cyber security.
Visibility + Evidence = SecOps
We exist to evolve your cyber security approach from promise-based to evidence-based, from probably secure to provably secure
What Do you Get:
We offer end-to-end SecOps infrastructure to security teams, providing a full-stack platform that captures and correlates all types of security data, integrated threat intelligence, automation, SOC workflows, alerting, and a 24x7 team of cybersecurity experts, ready to support you.
from DIY SOC:
Another option is to build your own Security Operations capability, deploying multiple tools for complete visibility and control over your data. However, this is a lengthy and expensive process, taking several months and significant investment in technology and personnel.from SOC/MDR providers:
Most SOC and MDR providers offer limited coverage of your enterprise, often focusing on specific areas or data sources. You often will find that your data is being trapped in a "black box" where you have limited visibility and control over the insights and findings. It can make it difficult to correlate and analyze data across different systems and platforms, leading to missed threats or delayed response times.
Peter RobinsonPeter Robinson

Mark MottersheadCOO, DataProtech Group

Ross ForgioneCIO, Johnson Winter & Slattery