Your last line of defense
Our SecOps platform includes a fully customizable hacker deception toolset that can be deployed for you.
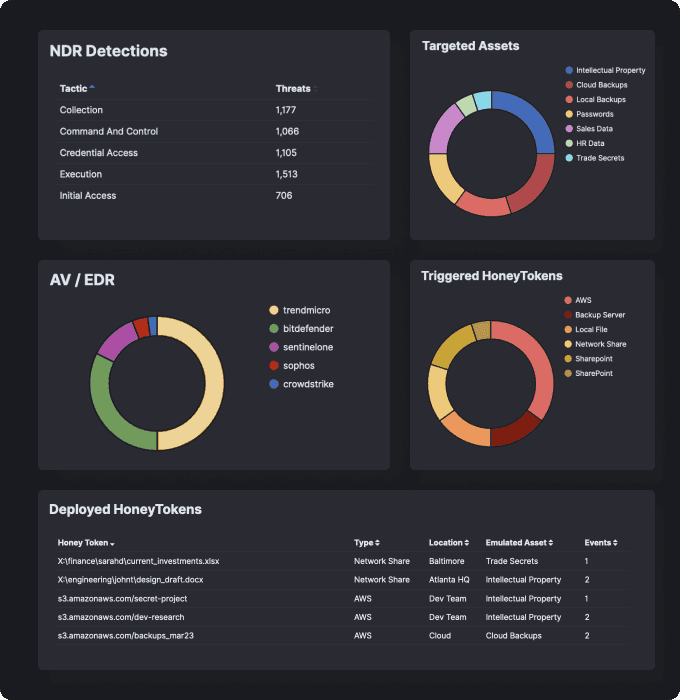
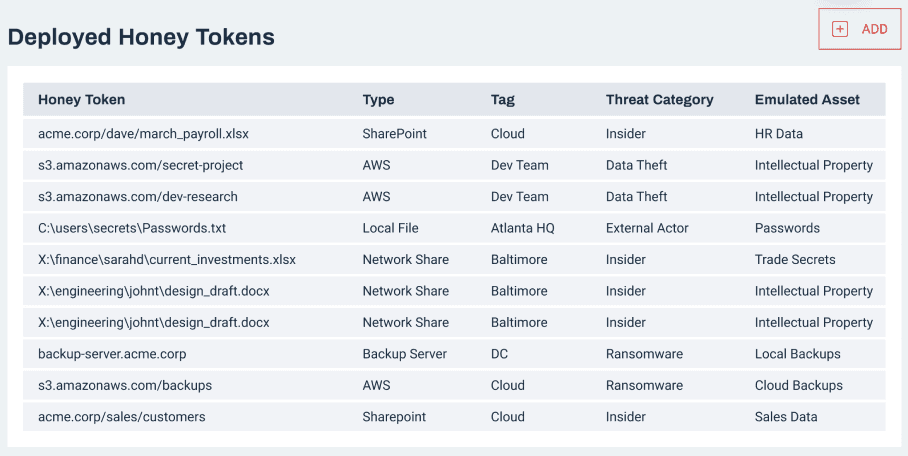
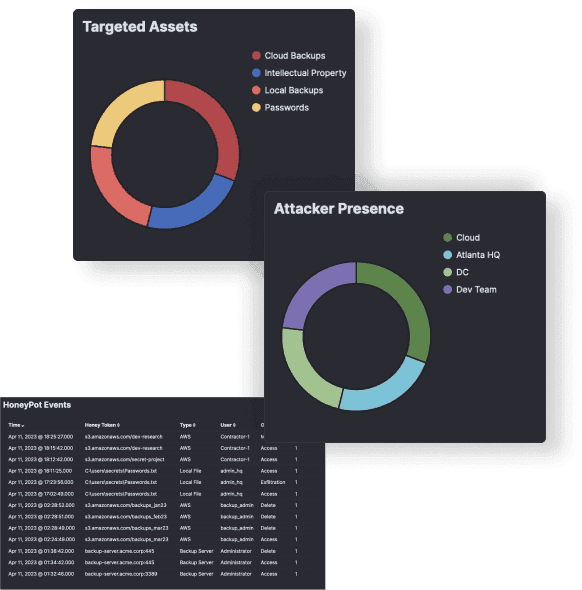
Deception tools like honeypots and honeytokens allow easy and reliable detection of malicious activities of sophisticated threat actors who managed to breach defenses.
Stay one step ahead of hackers
Get High Fidelity Detections
Lure threat actors into virtual honeypots and get detections with 100% confidence, not leaving them a chance to evade your defenses.Detect Lateral Movement
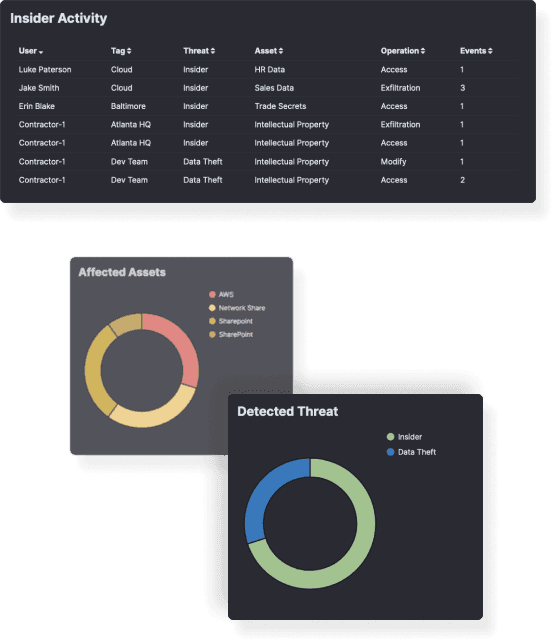
Pick-up hackers seeking ways to elevate their access and searching for vulnerable systems, confidential data, password files and other information.Stop Malicious Insiders
Catch insiders exploring your system with a malicious intent and trying to access intellectual property, HR data, codebases and other sensitive data.