Build Your Own Security Operations
Get started for free without any upfront investment - all platform features are available to you immediately.
You can leverage our hosted SaaS deployment, or deploy our platform in your private cloud - in any case, the platform can be tightly integrated in your operational processes, from customer onboarding to incident response.

Jacob ThankachenCEO, CybrHawk

Mark MottersheadCOO, DataProtech Group
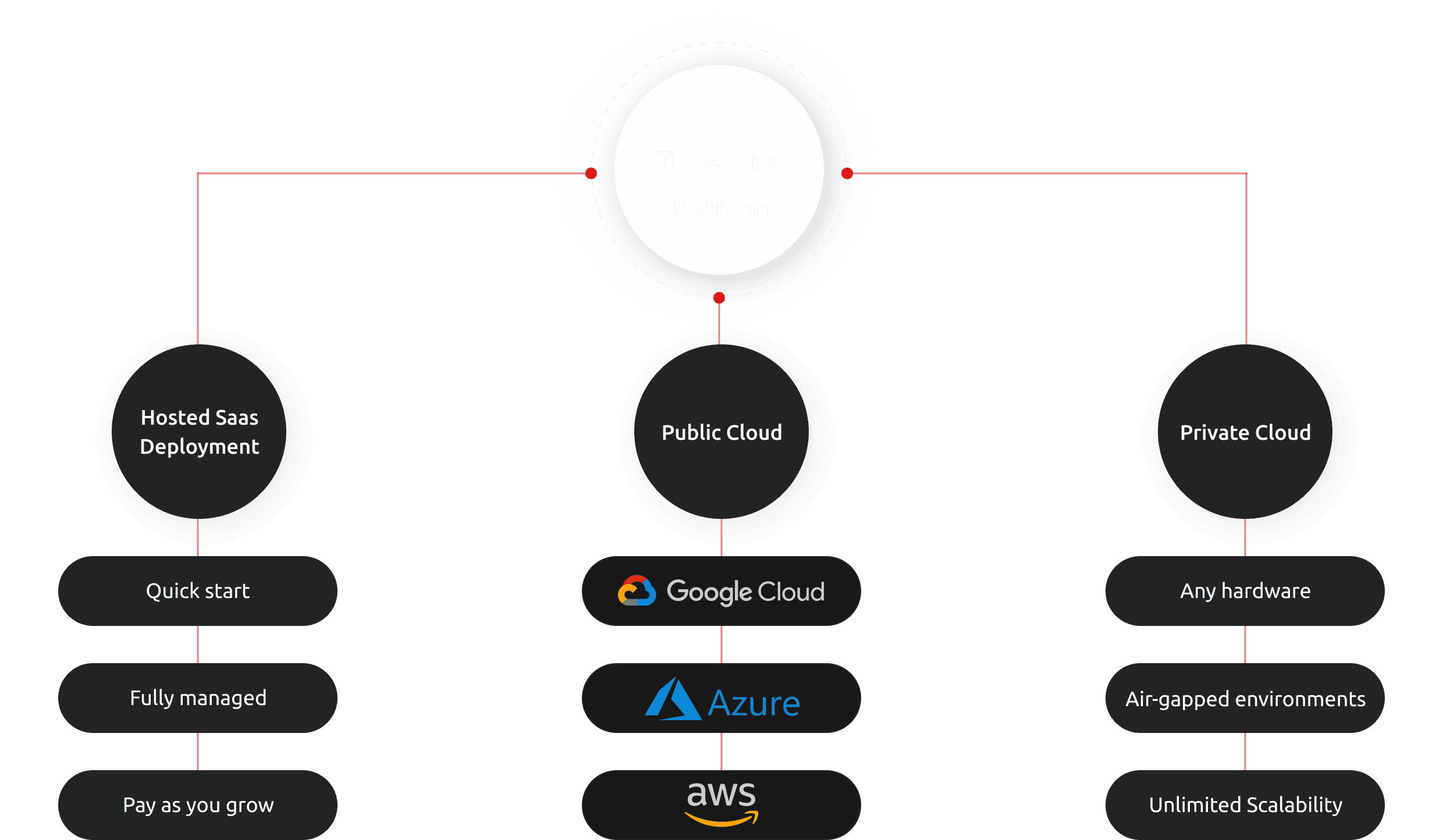
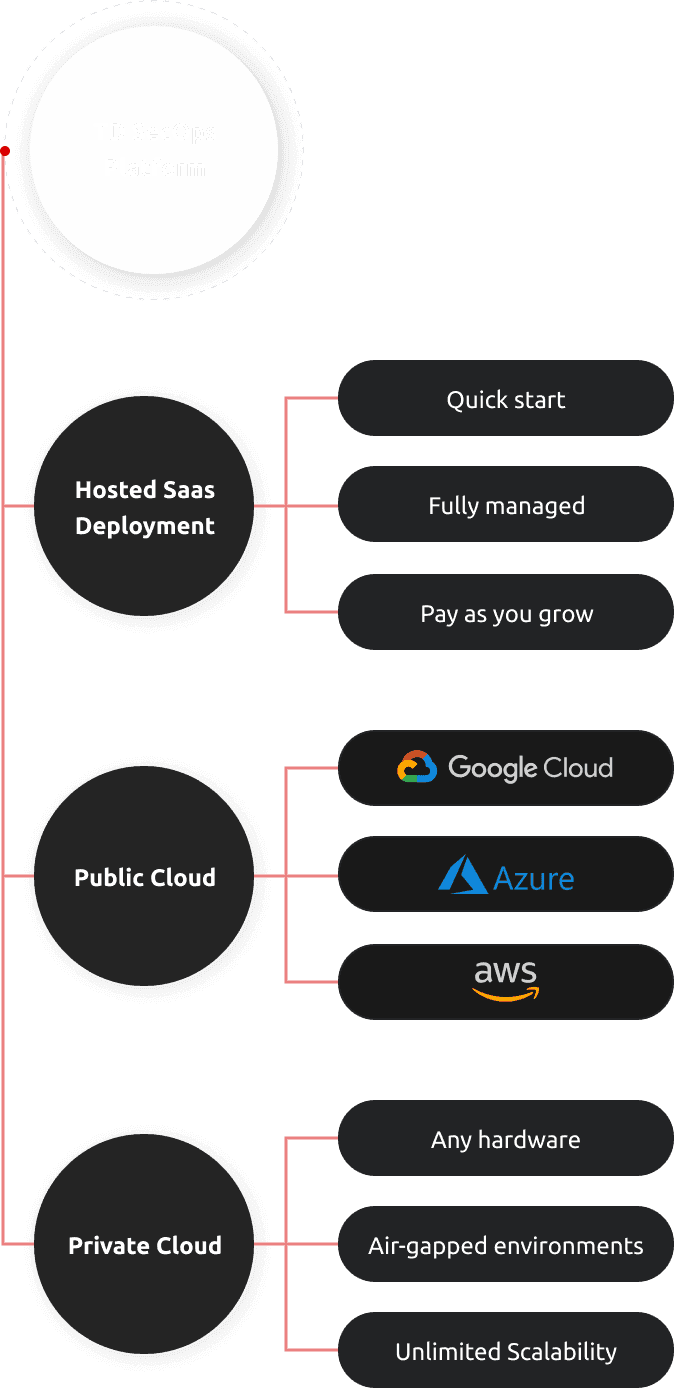
Flexible Deployment Options
We provide various deployment options. You can use our hosted SaaS platform, still running on your own domain with your custom branding. Alternatively, you can run your own instance.
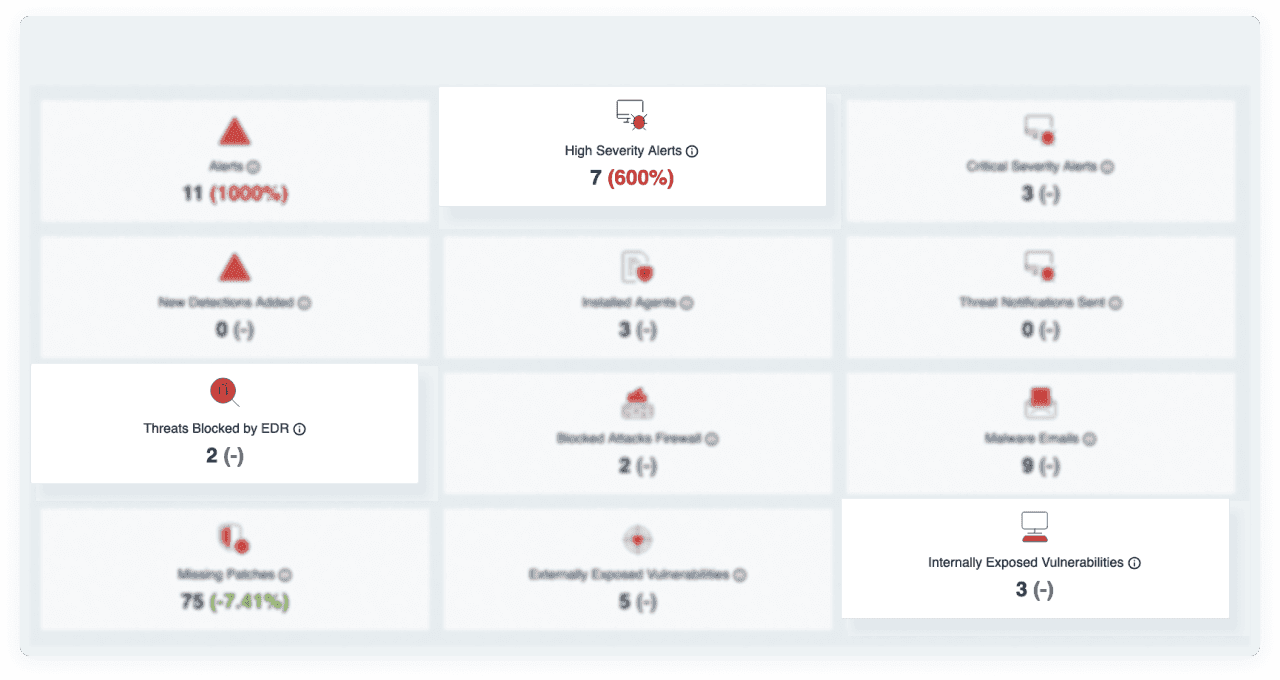
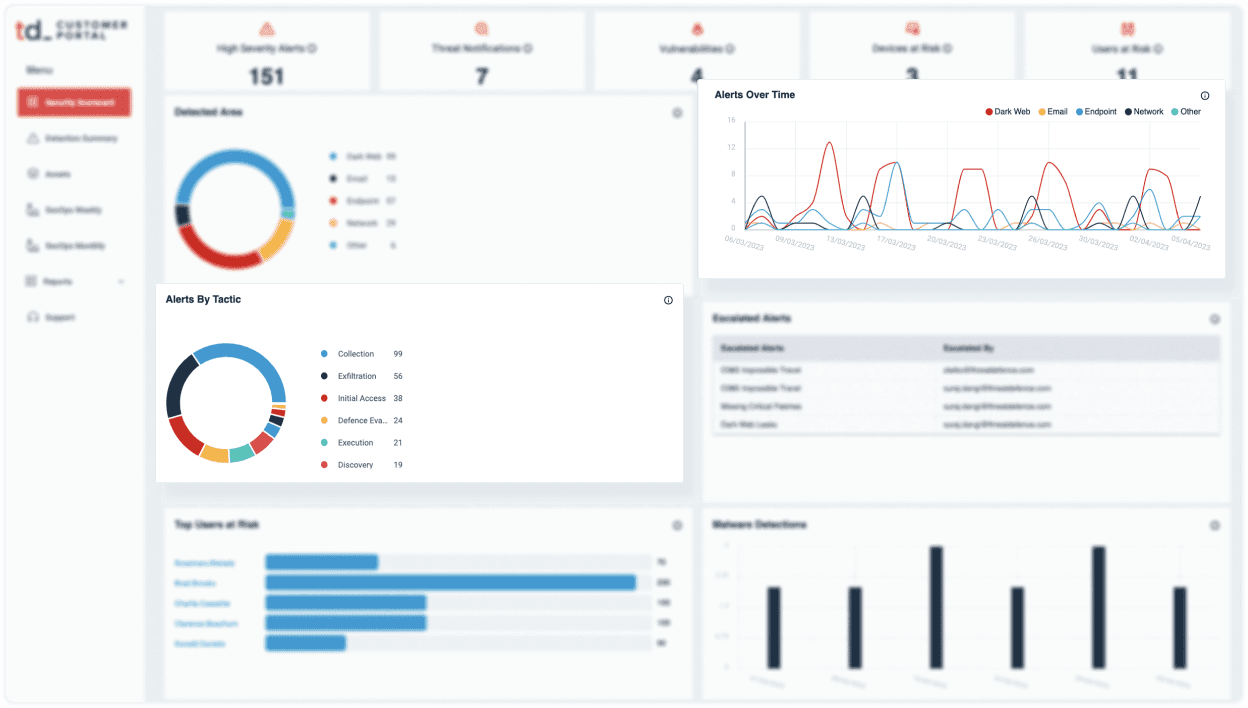
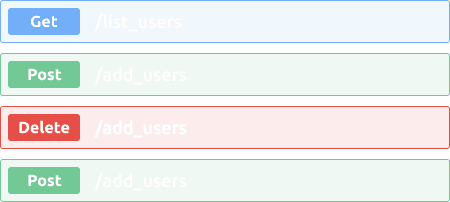
Integrate with Anything
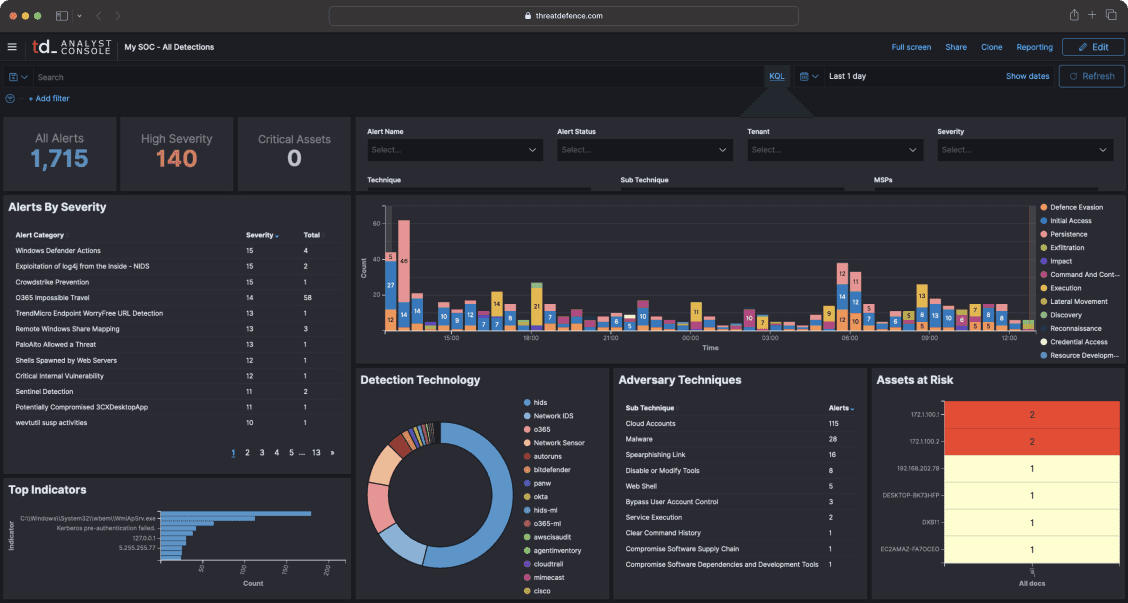
Use hundreds of out-of-the-box integrations to integrate any log source or application from your customer environment.
We guarantee that any API or log source can be integrated if it provides value from cyber security threat detection perspective - talk to our team and we will build a custom integration for you.
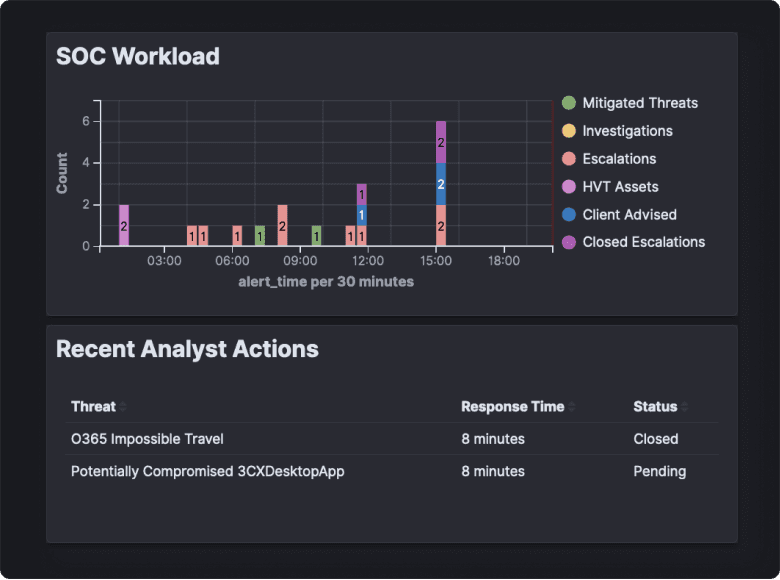
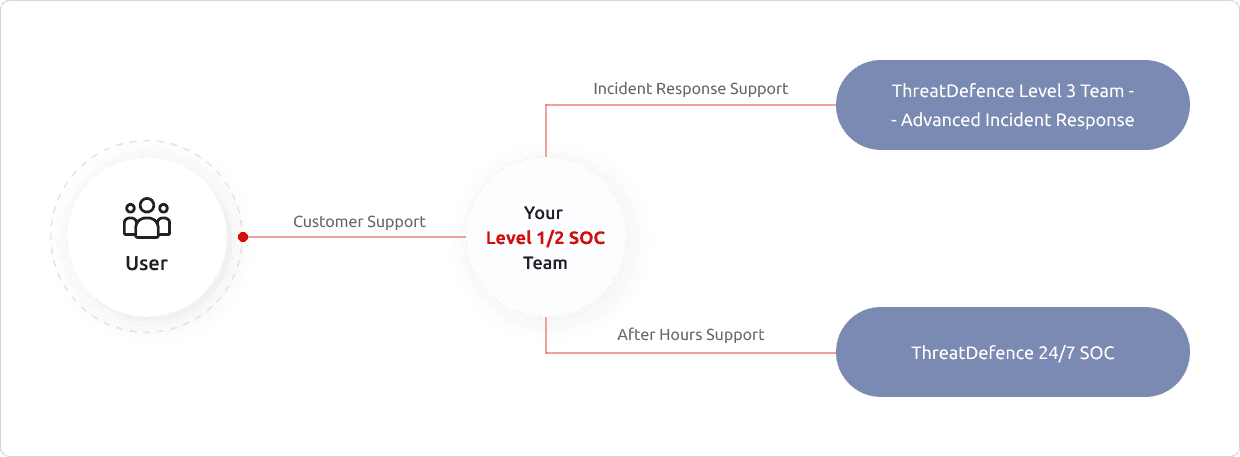
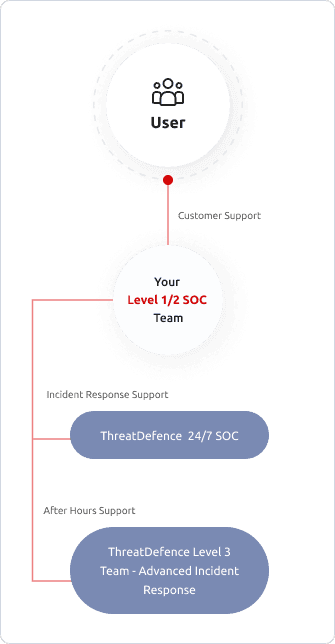
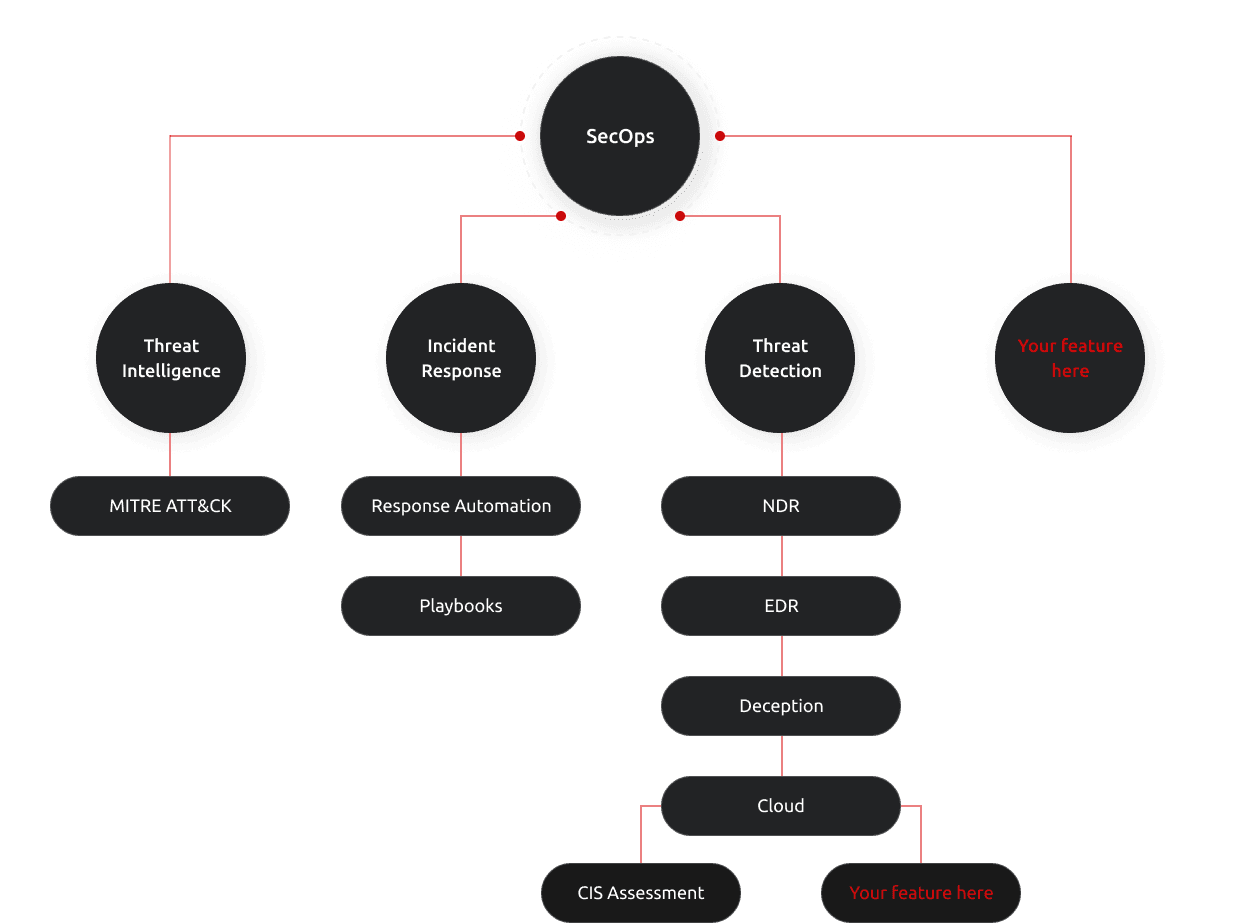
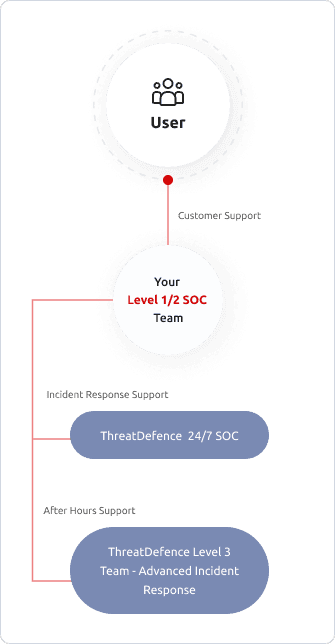
Augment Your SOC Team
it is not easy (and not cheap!) to staff and operate a 24x7 SOC team. As you mature and grow your Security Operations capability, you can transition through our flexible support models and use as much support as you need.
You can start by leveraging our 24x7 team, move into a hybrid after-hours support mode, and finally transition to a complete 24x7 internal SOC team if you like - you can still come to us for advanced support during incident response and investigations.