Implement Your Cyber Resilience Strategy
Many organizations tend to implement their governance, risk, and compliance practices independently of their operational cybersecurity capabilities. This often results in excessive work solely focused on organizational policies and procedures. The cybersecurity outcomes are not being measured, and it is assumed that the procedures will work - this is what we call promise-based security.
As a result, it is difficult to determine if your business is truly secure, and probably no one in your organization knows. In other words, there is no assurance. At ThreatDefence, we prefer to focus on the practical aspects of cybersecurity governance, building efficient capabilities to protect your business and maintaining ongoing assurance of your cybersecurity program.
WHAT OUR CUSTOMERS SAY ABOUT US

Peter RobinsonHead of Security, Zip Money
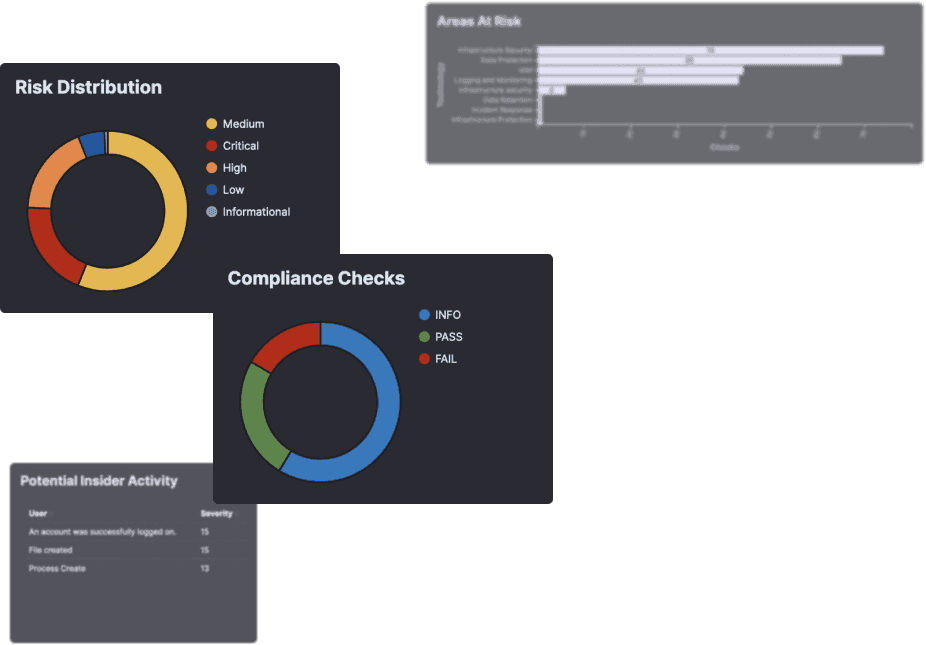
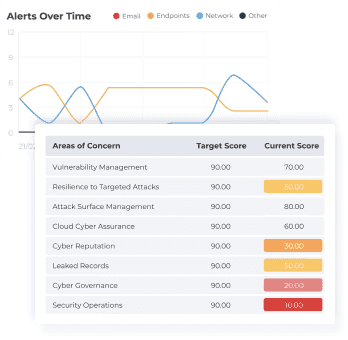
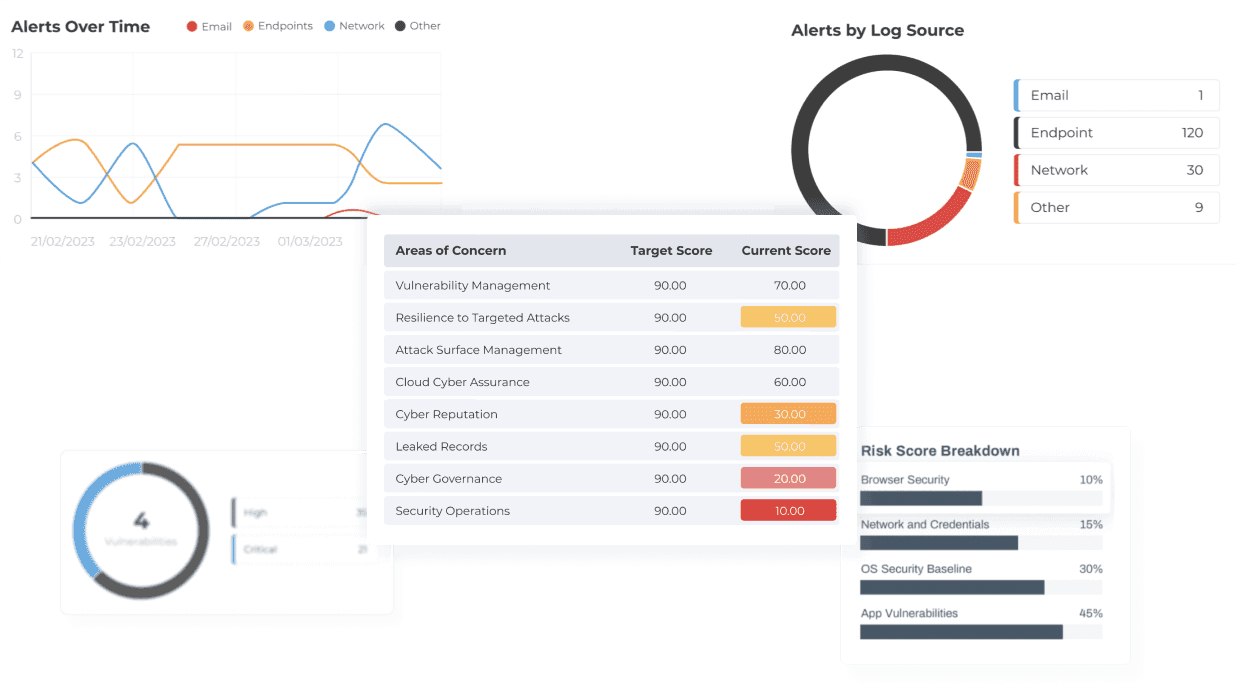
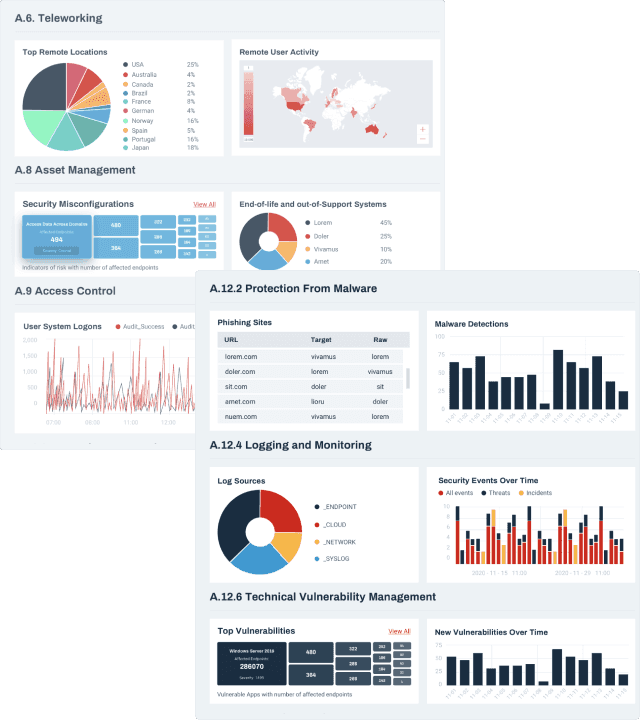
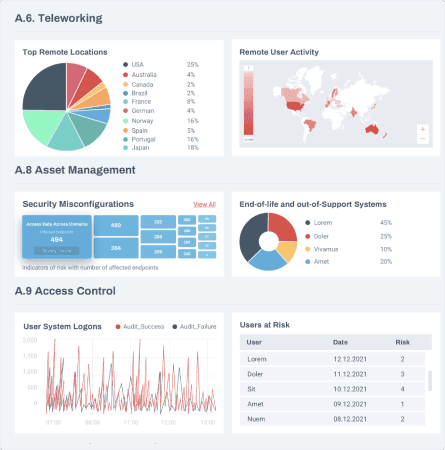
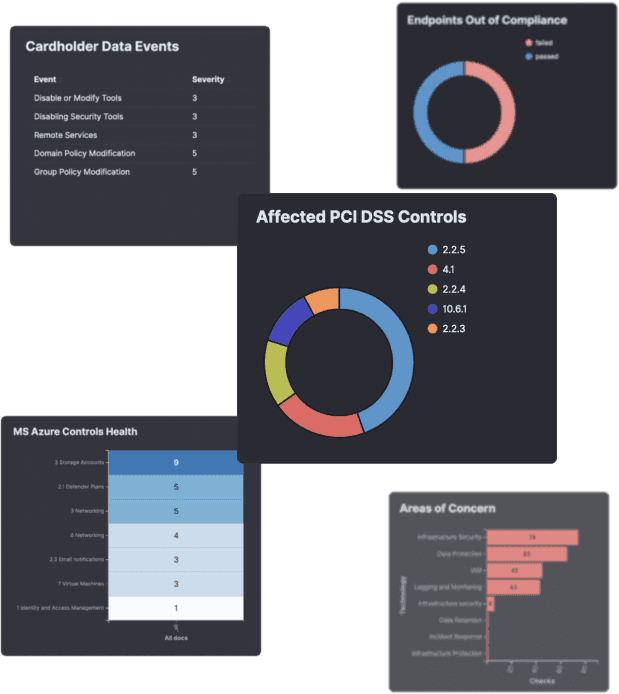
REPORT ON YOUR CYBER RISKS
We provide automated weekly and monthly reporting based on their operational and compliance needs. We will work with you to customize your report templates based on your technology stack and will ensure you all the information that you need.
Managed Risk Services
ThreatDefence offers Managed Risk Services tailored to your business needs, helping you to remain proactive, prioritize your cyber security program, and strengthen your defenses based on what is needed for your business.