Meet Evidence-Based SecOps
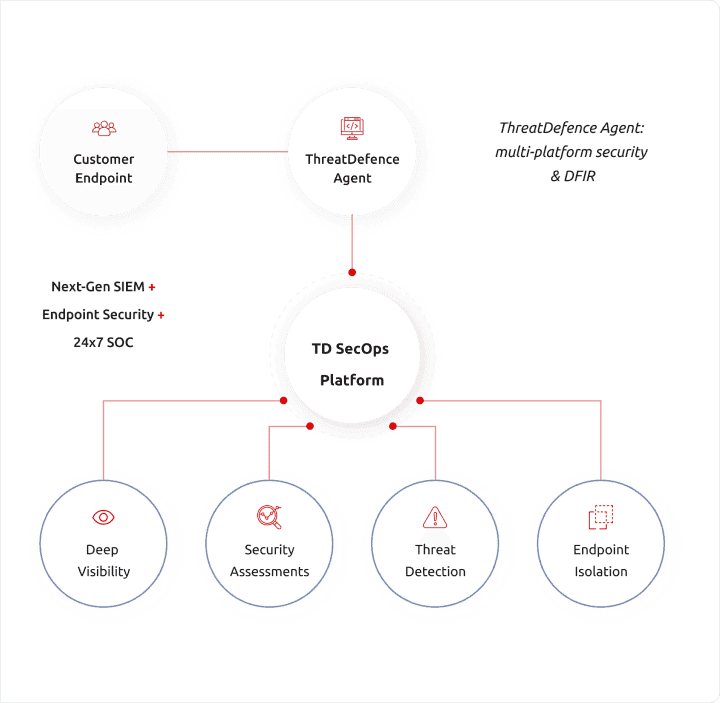
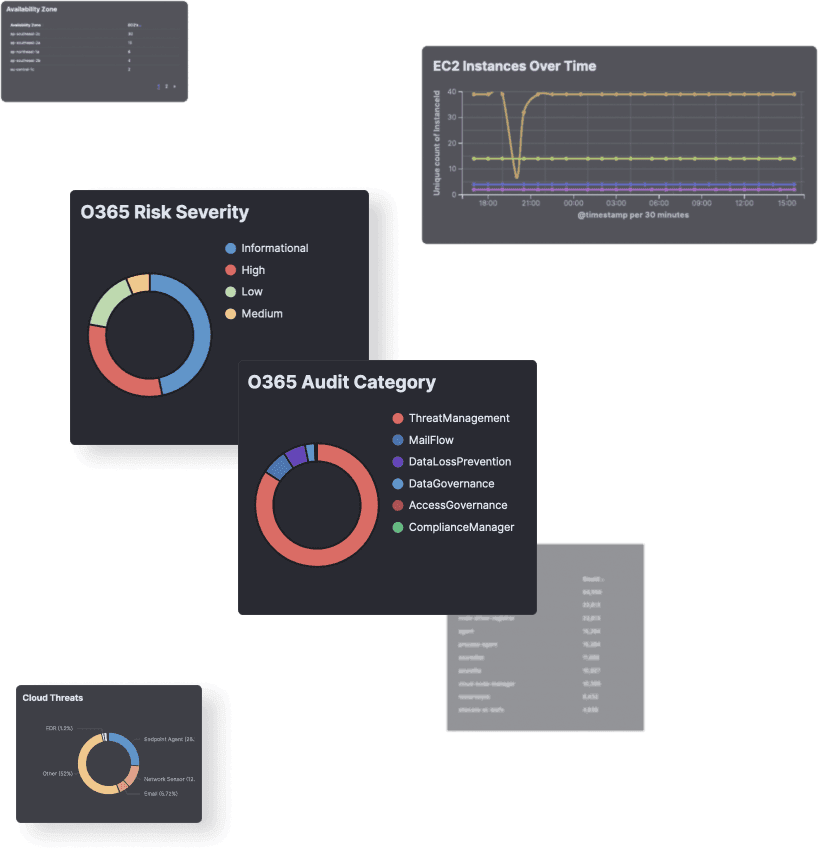
At ThreatDefence, we believe in giving you unrestricted access to your security data and providing comprehensive visibility across your entire IT stack. Our platform empowers you to establish an effective and sustainable Security Operations capability by transforming your data into actionable evidence.
We work with you to integrate people, processes, and technology that align with your unique needs and budget, so you can confidently implement a solution that works for you.
What Our Customers Say About Us

Peter RobinsonHead of Security, Zip Money

Ari AichHead of Technology, Campbelltown City Council

Ross ForgioneCIO, Johnson Winter & Slattery
Optimize Your SIEM Investment
We have observed many organizations investing in stand-alone SIEM platforms from global vendors. However, these platforms need dedicated personnel for management and to keep security content up-to-date.
At the same time, they do not provide any additional visibility beyond what can be collected from standard log sources such as syslog or Windows security events. To add and integrate features like vulnerability management, network detection and response, extended endpoint detection and response, and cloud visibility and threat detection, further investment in other security tools is required.
At ThreatDefence, we ensure that your SIEM capability covers your entire enterprise, providing your team with all the necessary data, findings, insights, and guidance needed to effectively respond to potential threats.
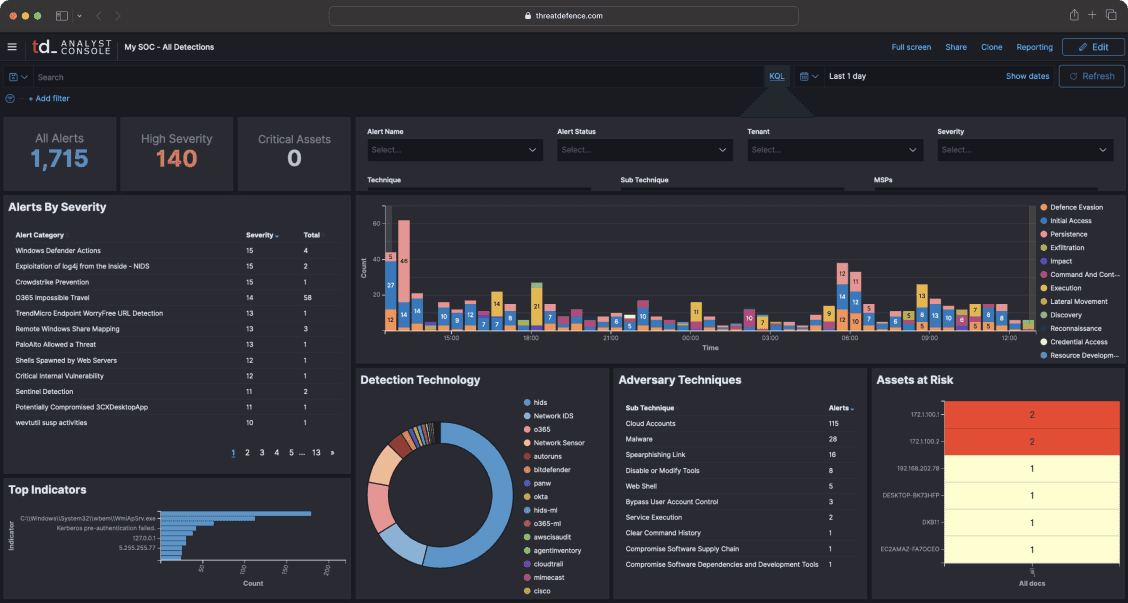
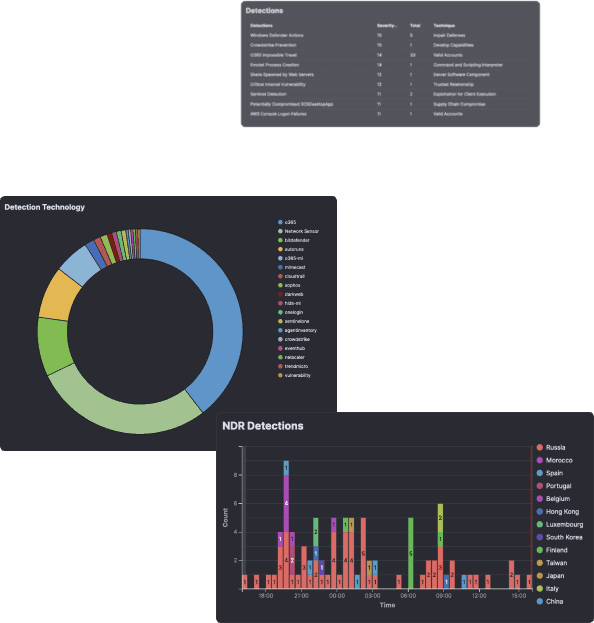
Full Access to Your Data
Get full access to your platform instance and your data, including all underlying security events and other telemetry collected from endpoints, networks and cloud systems.Attack Simulation and Training Data
Get access to sanitized data recorded during real cyber attacks, and run simulated cyber incident exercises.Joint Reviews and Training
Use our interactive review and knowledge sharing sessions to get cyber security recommendations and up-skill your team.Direct Communication
Talk directly to engineers and threat hunters and ask our core team anything in real-time.
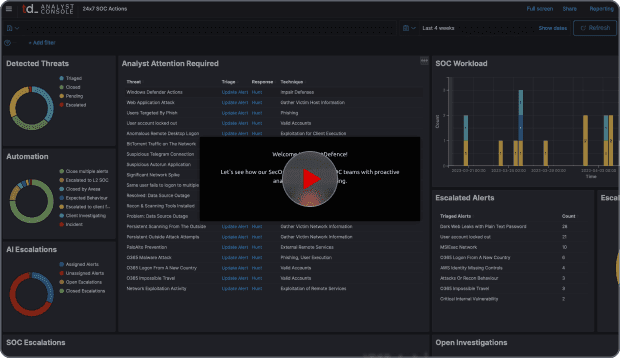
Continuous Monitoring
We monitor security events and detect threats in real-time, 24 hours a day. Our system processes your data non-stop and provide true correlation and detection in real-time.Security Geeks
We hire people who understand cyber security and love technology. They extend your existing team organically, to keep you secure.Threat Intelligence
We understand cyber security and know how it works - we always consider real-world detection scenarios, not just alerts and thresholds.
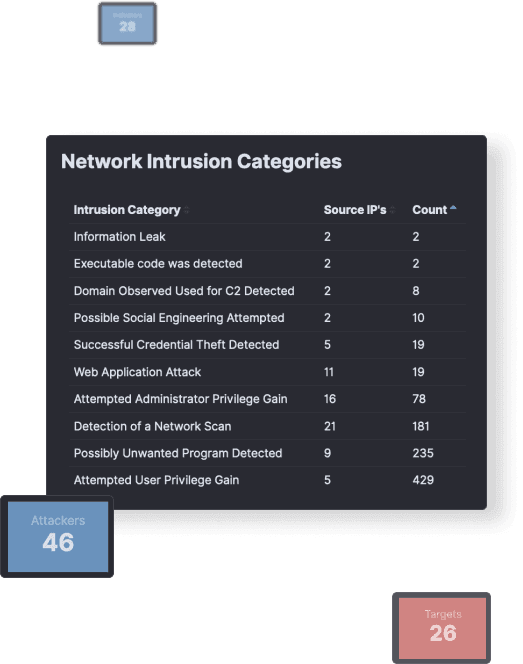
Digital Forensics and Incident Response
Every second counts when you are under attack and adversaries are browsing unrestrictedly through your network.
At ThreatDefence, we don’t spend hours and days searching through your systems. We use our technology to quickly get visibility and pinpoint attacker, suppress the threat as fast as possible and help you to recover from the breach and get back to normal operations.
- Full attack chain with real-time data ingestion from network, endpoint, cloud and syslog data.
- Access to threat intelligence and the latest insights from our incident response team.
- Detection capabilities mapped to MITRE ATT&CK framework.
- Dedicated threat hunters with years of expertise for deeper manual investigation and analysis.
- Machine learning and AI-powered detections integrated into our SecOps platform.